A new Emotet phishing effort targets U.S. taxpayers by imitating W-9 tax paperwork purportedly delivered by the Internal Revenue Agency and your business partners.
Emotet is a renowned malware infection that has historically been delivered by phishing emails including Microsoft Word and Excel documents with malicious macros that install the virus.
Once Microsoft began restricting macros in downloaded Office documents by default, Emotet moved to exploiting Microsoft OneNote files with embedded scripts to install its malware.
Once Emotet is installed, the malware will harvest victims’ emails for future reply-chain assaults, send further spam emails, and finally install other malware that provides initial access to other threat actors, such as ransomware gangs.
Emotet prepares for the next US tax season
The Emotet virus uses themed phishing attacks to correspond with holidays and annual business events, such as the current U.S. tax season.
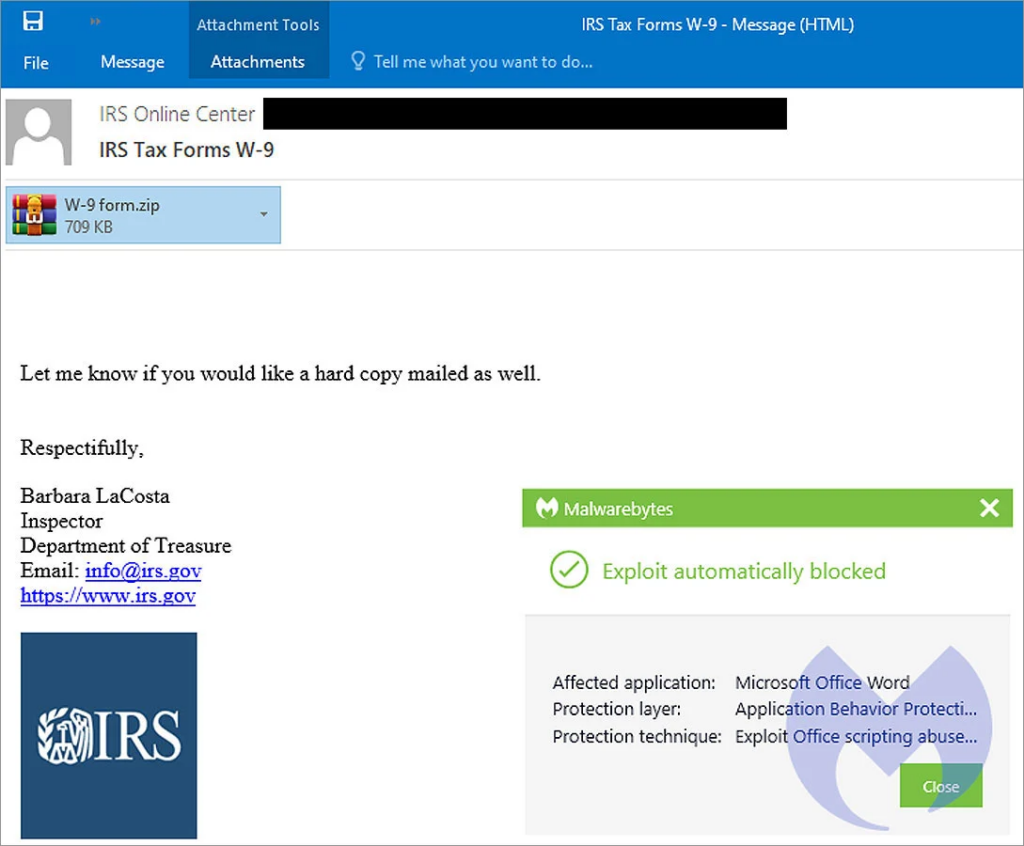
In recent phishing attempts seen by researchers at Malwarebytes and Palo Alto Networks Unit42, the Emotet virus targets victims with emails containing bogus W-9 tax form attachments.
In the campaign seen by Malwarebytes, threat actors send emails named ‘IRS Tax Forms W-9’ while posing as Internal Revenue Service inspectors.
These phishing emails contain a ZIP file entitled “W-9 form.zip” that contains a malicious Microsoft Word document. This Word file has been inflated to over 500 MB in order to make it more difficult for security tools to identify it as malicious.
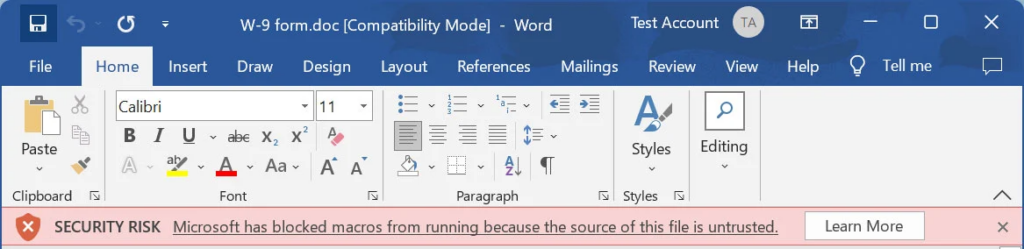
Nevertheless, now that Microsoft blocks macros by default, users are less likely to enable the macros and become infected through malicious Word documents.
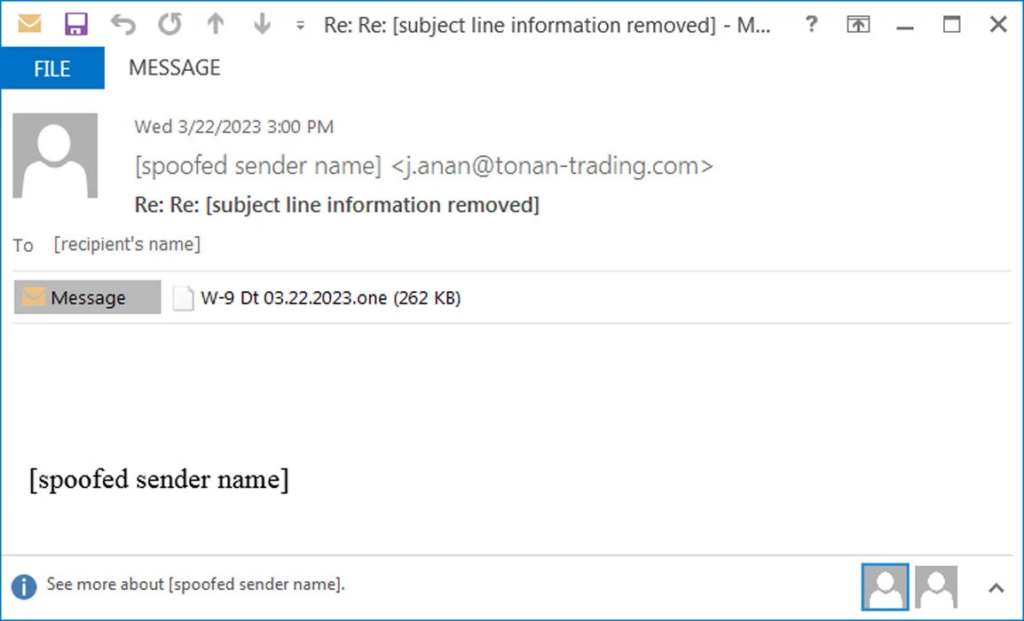
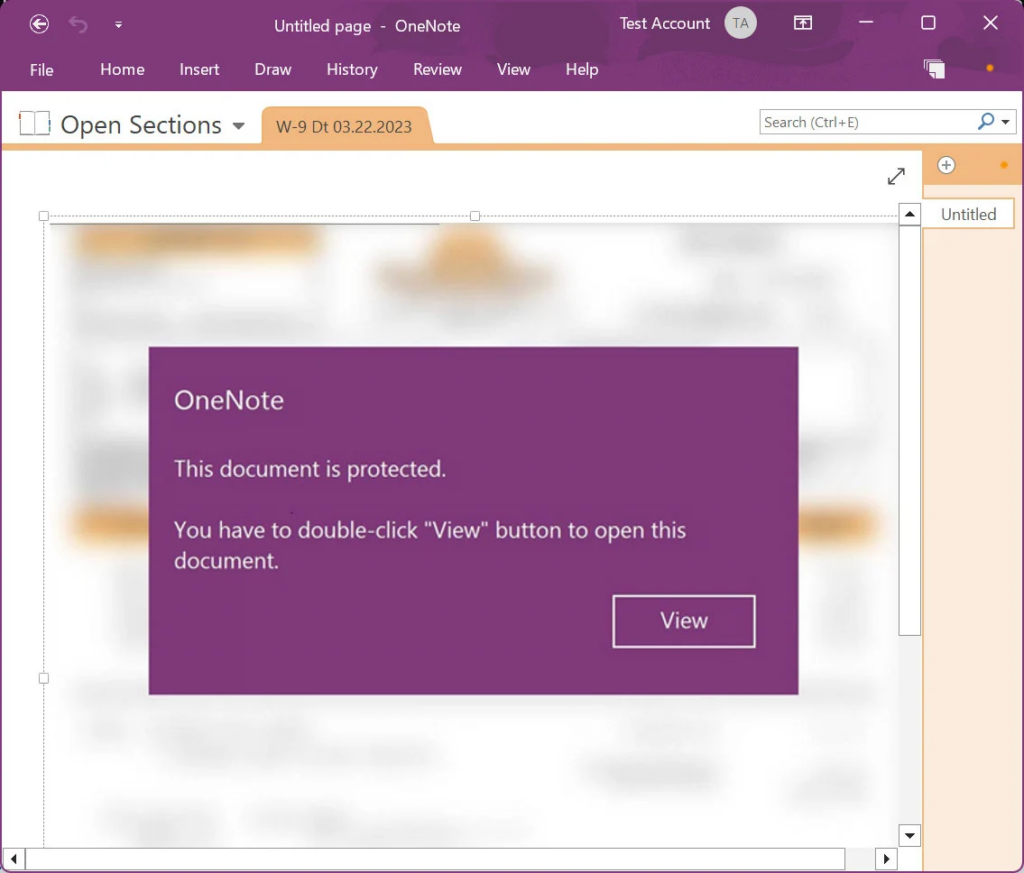
Threat actors circumvent these constraints in a phishing campaign observed by Brad Duncan of Unit42 by employing Microsoft OneNote documents with embedded VBScript files that install the Emotet virus.
This phishing attempt uses reply-chain emails posing as business partners sending W-9 Forms.
Microsoft OneNote will alert the user that the embedded VBScript file may be harmful before starting the file. Regrettably, the past has shown us that many users disregard these warnings and just permit the files to execute.
Once the VBScript has been executed, it will download the Emotet DLL and launch it with regsvr32.exe.
The virus will now operate stealthily in the background, capturing email and contacts while awaiting the installation of more payloads.
If you receive emails purporting to be W-9 or other tax forms, you should first examine the attachments with local antivirus software. Due to the sensitive nature of these forms, it is not recommended that they be uploaded to cloud-based scanning services such as VirusTotal.
Typically, tax forms are given as PDF files and not as Word attachments; thus, if you receive a Word attachment, you should refrain from opening it and allowing macros.
Lastly, it is unlikely that tax forms would ever be transmitted as OneNote documents, so if you receive such an email, delete it immediately and do not read it.
Always, the greatest line of protection is to delete emails from unknown senders, and if you know the sender, call them by phone to confirm that they sent the email.

